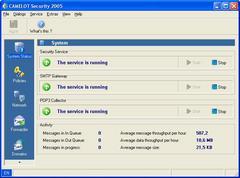
CAMELOT Security 2005 is a server side based spam filtering solution for MS Windows platforms. Incoming messages run through a chain of different application layers inside a multi-tier protection system. Several methods of analysis are executed by active content processors, using artificial intelligence with self-learning filter processes. A special SMTP gateway verifies the identity of the sending instance and denies all further processing as soon as an invalid incident occurs. This prevents unauthorized access before the message is delivered to the regular mail system. A structured profile set, based on network and account attributes, is used to address message contents in consideration of different requirements. Individual anti spam rules are executed, depending on the related user or network location. The evaluation of unknown content schemes takes effect by Bayesian classification methods. Intelligent content processors identify the appropriate category by calculating the conditional probability of the affected content. Also pornographic contents in images can be detected in this way. Well known anti virus products can be integrated to prevent virus infection. A special interface to Norman Virus Control offers a proactive solution to protect the system against new and unknown viruses. Multiple messages are processed simultaneous in a multi threaded environment. This guarantees unrestricted email transfer, even if the system is busy with single large messages. The usage of SQL databases for the storage of generated pool data provides high performance also in large messaging environments. The message processing is server side based and thus controlled at a centralized level. This protects the rest of the network from dangerous contents. Explicit boundaries between secure and insecure areas are set in this way. This minimizes the remaining risk, caused by weak points somewhere in the network.