Overview |
 Comments (0) |
 Ratings (0) |
 Download |

|
||||||||||||||||||||
|
Search
Software
Advertisements!
Free-downloads
|
Options for File Own Guard
Advertisement
File Own Guard
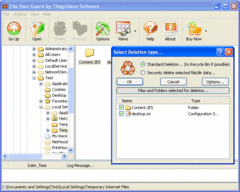
The File Own Guard allows you to choose from wide range of crypto-algorithms so that you may be firmly convinced that the information wont be accessed without your permission. FOG has useful ability to create Self-Extracting crypto-archives. Such types of archives make work with data more comfortable and effective when e-mailing or using removable media. The File Own Guard also achieves a secure removal of your sensitive data by overwriting the file before deleting it using one of the eight special algorithm, and then destroying the file size, cluster number, time meta data for that file, etc. Our software uses the newest and the strongest algorithms and methods to make your files and data secure. So we have made number of tests to make sure that our program is 'Back-doors' free! The File Own Guard has User-friendly Windows Explorer like interface. Most file explorer features are supported. To make our customer feel comfortable with our software we included Easy to use full-scale Help system. Free for personal use! Advertisement
|
|||||||||||||||||||