Overview |
 Comments (0) |
 Ratings (0) |
 Download |

|
||||||||||||||||||||
|
Search
Software
Advertisements!
Free-downloads
|
Options for IP Traffic Monitor
Advertisement
IP Traffic Monitor
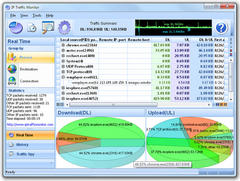
Recently I've come across a wonderful utility that serves just this purpose. IP Traffic Monitor sits in your system tray and monitors all your network connections. You can either monitor the active connections in real-time or browse historical logs. The program shows extensive information about each connection: remote host IP, remote host name (if available), amounts of incoming and outgoing traffic through this connection, timestamps of the first and last activity of this connection, name of the process that initiated or accepted this connection, full path to the application the process belongs to, etc. The traffic summary indicator shows an upload and download speed graph and traffic totals. In addition it draws pie chart diagrams that illustrate the percentage of certain hosts in the total incoming and outgoing traffic. It would be naive to expect packet sniffer functionality from a $19.95 utility. Yet, IP Traffic Monitor includes a full-featured sniffer. You can easily capture and analyze TCP packets. Captured packets can be saved to a log file or analyzed in place. For example, you can analyze HTTP requests including passwords and other data that is sent to servers from your PC. Advertisement
|
|||||||||||||||||||